What Is RDP—Find Everything You Want to Know Here
What is RDP? Read this article to fully understand its basic meaning, working principle, characteristics, functions, etc.
What is RDP used for?
What is Remote Desktop Protocol or we can say what is RDP? It is a secure network communication protocol developed by Microsoft, which can be used as an extension of the Standard Protocol T.120 as part of the ITU (International Telecommunication Union). It is worth noting that some versions of RDP can be used in Linux, Unix, Mac, iOS, Android, and other systems in addition to Windows.
Users use RDP clients to connect to a Windows computer or a Server, for example, Remote Desktop Windows Server 2016, and the connected computer or Server also needs to run RDP at the same time. RDC (Remote Desktop Connection) is one of the RDP clients, also commonly known as RDP. As for the main function of RDP, to put it simply, it allows users to control any PC remotely through a graphical interface, just like they are actually using it.
Then what is RDP used for? RDP can be used for remote access, remote assistance, and remote support. It is mostly used for business purposes in life. But you need to distinguish it from cloud services. In cloud services, the content that users actually access is files and applications stored in the cloud (cloud server). When using RDP, the user is actually accessing files and applications stored locally on the host computer (the controlled computer).
How does RDP work?
Before we have a deep understanding of the working principle of RDP, we need to clarify what protocols or standards RDP has:
TPKT: It is an ISO transmission service on top of TCP (Transmission Control Protocol), which allows the two groups to exchange information units of TPDU (Transmission Protocol Data Unit) or PDU (Protocol Data Unit).
X.224: It is a connection transmission protocol that can provide a connection-mode transmission service, which is mainly used in RDP initial connection requests and responses.
T.125 MCS: It is a multi-point communication service that allows RDP to communicate and manage through multiple channels.
To put it simply, the working principle of RDP is to realize the exchange of information units through TPKT, establish a connection through X.224, and use T.125 MCS to open multiple channels to complete the back and forth data transmission between two devices. The mouse, keyboard activities, and other data controlled by the user are all sent to a dedicated port using TCP/IP, and then transmitted to the connected remote desktop, just like a remote control toy car or drone. The user remotely controls them by transmitting commands. And the port is 3389 by default.
The RDP connection process can be divided into the following 9 stages in order:
- Connection Initiation
- Basic Settings Exchange
- Channel Connection
- Security Commencement
- Security Settings Exchange
- Licensing
- Capabilities Exchange
- Connection Finalization
- Data Exchange
Connection Initiation
RDP connection is initiated by the client using X.224 connection request PDU, including some security protocols and connection flags supported by the client. These agreements can be divided into:
- Standard RDP security:
-RSA RC4 encryption defaults
- Enhance RDP Security TLS:
-TLS (Transport Layer Security Protocol)
-CredSSP encrypted data (TLS + NTLM / Kerberos)
-RDSTLS (an enhanced RDP variant)
At this time, the server will also confirm the PDU connection through the X.224 connection. The packet contains an RDP negotiation response, which is used to inform the client that the selected security protocol (selected from the protocols supported by the client) will be used in the whole connection life cycle.
Basic Settings Exchange
At this stage, the client and server rely on the basic exchange settings of the connection between MCS and initial PDU and the response of MCS connection to PDU. The above settings can be divided into:
- Core data: RDP version, desktop resolution, color depth, keyboard information, hostname, client software information (product ID, version number), etc.
- Security data: encryption method, session key size, server random number (create session key), and the server certificate (used for standard RDP security).
- Network data: request information about virtual channels and allocate virtual channels. Including the number of channels and a specific set of virtual channels.
Channel Connection
When the list of virtual channels used by the RDP session is created, each individual channel connection is established. It can be divided into several sub-stages in order:
- MCS vertical domain request: the height of the MSC domain, usually is 0.
- MCS additional user request: require user channel ID.
- MCS additional user confirmation: user channel ID.
- MCS channel join request and confirmation: the client will start to use their ID to request to join the virtual channel, and the server will confirm the success of each channel in turn.
Security Commencement
At this stage, the client will send a secure exchange PDU containing the public key of the server with random encryption. The client and server will then create a session encryption key with random numbers (secure data and secure exchange PDU from basic settings exchange). Subsequent RDP traffic will be encrypted at this time.
Security Settings Exchange
At this stage, the client will send an encrypted client information PDU containing the supported compression type, user domain, user name, password, working directory, and so on.
Licensing
This stage mainly allows authorized users to connect to the terminal server. Two or more server connections can be supported at the same time, but this requires acquiring a Microsoft license. In most cases, the RDP server is not configured with a license server, so the RDP server will only send a PDU (up to two sessions) to the licensed client.
Capabilities Exchange
At this stage, the server will send the supported functionality in a demand-active PDU that includes 28 different types of capability sets, generic (operating system version, generic compression), input (keyboard type and functionality, fast path support, etc.), fonts, virtual channels, bitmap codecs, etc. In this case, the server may send a monitor layout PDU to describe all monitors, while the client will respond with a set of functional confirmation active PDUs.
Connection Finalization
At this stage, the client exchanges several types of PDUs with the server to complete the connection. These PDUs come from the client, including several types:
- Client/Server synchronize PDU: used to synchronize user identifiers between client and server.
- Client/Server control PDU (collaboration): Client and server complete shared control of the session by sending this PDU.
- Client control PDU (request/grant control): The client sends a control request and the server grants it.
- Permanent Key List PDU/PDUs (optional): Clients send a list of keys to the server, each identifying a cached bitmap. This also allows the bitmap cache, a mechanism for reducing the network traffic required to transfer graphics output from the server to the client, to be persisted. But this persistence is contrary to the life cycle constrained by connections.
- Font List/Mapped PDUs: These PDUs are used to store font information (font name, average width, signature, etc.) in sessions, but Microsoft does not seem to use them.
Data Exchange
When the connection is completed, the data sent between the client and the server is mainly input data (from the client to the server) and graphic data (from the server to the client). In this case, additional data transferred includes connection management information and virtual channel messages.
It is important to note that mouse, keyboard activity, and other data need to be encrypted before they can be transmitted over the Internet, which often results in delays. For example, when you want to double-click an application to open it, you may need to wait a few milliseconds for feedback.
What are the features and functions of RDP?
As a secure and interactive protocol, RDP can build a secure connection channel between clients, servers, and virtual machines across different Windows system versions and devices in order to protect remote connections. Next, I will introduce the features and functions of RDP to you in detail:
- It supports up to 32-bit color and 64000 independent data transmission channels.
- Through the RC4 encryption algorithm, the data is encrypted with a 128-bit secret key and supports TSL (transport layer security).
- It can redirect the audio of the remote desktop to the local computer.
- It supports network-level authentication.
- It supports multiple displays.
- The user can refer to the file system on the local (client) computer while using the remote computer.
- When the connection is temporarily disconnected, there is no need to log off the remote session.
- You can use the local printer for the remote desktop session.
- It supports session shadow (a kind of session mode of remote desktop, can also play the role of remote assistance).
- It can further reduce bandwidth and increase connection speed.
- The clipboard can be shared between the local computer and the remote computer.
- It supports RemoteFX virtualized GPU (graphics processing unit).
- The application program of the remote computer can be run on the local computer.
What is the use of RDP?
RDP can break through the limitations of space and let you experience remote control in the true sense, which is of extraordinary significance for both work and life. Next, let’s introduce the practical use of RDP to everyone.
- Improve productivity. The correct use of RDP allows users from all over the world to remotely control computers freely. In simple terms, work efficiency is improved. Whether it is temporarily arranged overtime tasks or documents that need to be processed urgently, RDP can be used to help users to complete these.
- Save costs. The flexible use of RDP allows users to freely connect their home desktops and company computers. This online remote office mode further saves additional laptop or mobile phone costs and intangibly saves a lot of money.
- Help you solve problems. Whether it is to complete the company’s unexpected overtime tasks or to help relatives and friends solve computer problems, RDP can be used to realize the remote connection to solve various problems encountered in life and work.
What are the advantages and disadvantages of RDP?
RDP, like a remote control solution with a large user base, undoubtedly has many advantages, which is why it has been widely acclaimed. But in fact, RDP has some unavoidable drawbacks that we should fully understand before using it. Next, we will give you a detailed description of the advantages and disadvantages of RDP.
The advantages of RDP:
- Compared to cloud services or other devices, RDP allows data to be safely stored on local devices.
- Remote connections can be made without using a virtual private network (VPN) exclusively.
- If your company has a traditional local IT infrastructure, remote control can be achieved.
The disadvantages of RDP:
- With slow network speeds, remote connections are prone to delays.
- RDP has certain security vulnerabilities and may be subject to network attacks for long-term use.
- It’s not applicable to all Windows versions. Windows 7 Starter/Home Edition, Windows 8/8.1 Home Edition, and Windows 10 Home Edition do not support Remote Desktop Connection (RDP). If you want to use it, please upgrade to the Professional or Enterprise version.
- When the two computers are on different networks, the configuration process is very complicated.
RDP security issues
Now that the security issues of RDP have been mentioned above, let’s introduce the well-known security vulnerabilities of RDP over the years in detail to you.
- In March 2012, Microsoft released an update to a critical RDP security vulnerability, which targeted a vulnerability that could allow unauthenticated clients and computer worms to damage Windows computers.
- In March 2018, Microsoft released a patch for CVE-2018-0886, which is mainly used to repair remote code execution vulnerabilities in CredSSP. The vulnerability involves security support providers for Microsoft Remote Desktop and Windows Remote Management.
- In May 2019, Microsoft released a security patch for CVE-2019-0708, which is mainly used to fix the vulnerability named “BlueKeep”. The vulnerability can spread by itself and poses a greater hazard.
- In July 2019, Microsoft released a security patch for CVE-2019-0887, which is an RDP vulnerability that affects Hyper-V.
How to safely use RDP
From the above point of view, RDP does have certain security risks. Therefore, in order to ensure the security of personal privacy and related data, we should learn how to use RDP safely. Next, I will introduce how to use RDP safely.
- Before using RDP, pay attention to enabling network-level authentication.
- Turn on the Firewall to prevent the RDP server from being exposed to the Internet.
- Set as complex passwords as possible, enable multi-factor authorization, and enable lockout strategies to prevent network attacks.
- Do not use an administrator account to connect remotely.
- Add fully trusted devices to the whitelist.
- Protect the port, even if RDP is not used.
- Enable automatic updates of RDP client or server software to ensure that you are using the latest version to reduce security vulnerabilities.
- Encrypted high-security VPNs can be used when connecting across networks, which is more secure than exposing the RDP server to the Internet.
How to remotely control PC over RDP
After learning what is Microsoft Remote Desktop, let's learn how to use it. RDP has a large user group. It is one of the most commonly used remote access software. It is very convenient to connect in the LAN environment, but it is difficult to connect in different network environments. Next, we’ll briefly introduce how to remotely control a PC over on the same network.
Set up the host computer
Step 1. Navigate here: Start > Settings > System > Remote Desktop, and turn on Enable Remote Desktop.
Step 2. Find User accounts and click Select users that can remotely access this PC.
Step 3. After opening the Remote Desktop Users window, click Add to add users who are allowed to access this computer (you need to add already existing users to realize remote desktop).
Start remote control on the client computer
Step 1. The client computer doesn’t need any configuration. Just search for Remote Desktop Connection in the Search box. And then open it.
Step 2. Enter the IP address and user name in the Remote Desktop Connection interface to achieve connection (if you don’t know what your computer’s IP address and user name are, follow the tutorial below).
How to query IP address and user name?
Step 1. Press Win + R to invoke the Run dialog box. Type in “cmd” and press OK. Then type “ipconfig” and press Enter. Now you can see a group of IP addresses, of which the IPv4 address is the one you need.
Step 2. Then type “query user” to see the username.
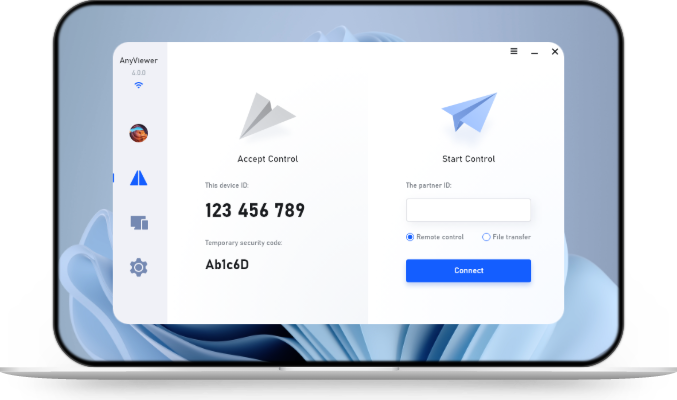
Free & easy Remote Desktop Connection alternative: AnyViewer
In addition to Remote Desktop Connection, here we would like to introduce another remote desktop tool to you, which is called AnyViewer. It has the following advantages over RDC:
- RDC requires an IP address or computer name to achieve remote connection, while AnyViewer doesn’t.
- RDC requires the two devices to be under the same network, while AnyViewer doesn’t.
- RDC can’t be used to connect to Windows 10 Home edition (some other editions as well), while AnyViewer supports any devices running iOS 10.0 or later and multiple Windows versions on PCs.
Besides, it also supports unattended remote access. Users can easily access an unattended computer with just one click as long as both devices are logged in to the same account. Let's see how to achieve it.
Step 1. Download, install, and launch AnyViewer on both computers.
Note: AnyViewer also has an iOS version, you are also able to remotely control your PC from your iPhone or iPad.
Step 2. Go to Log in, and then click Sign up. (If you already have signed up on its official website, you can log in directly.)
Step 3. Fill in the signup information.
Step 4. Then you can see you successfully logged in to AnyViewer. Your device will automatically be assigned to the account you've logged in to.
Step 5. Log in to the same AnyViewer account on the two devices, then click One-click control to achieve unattended remote access. You can also transfer files between computers.
Note: If you want to assign more devices to achieve unattended remote access, then you can upgrade your account to a Professional or Enterprise plan. Also, you can connect to another computer in privacy mode, which means you can black the screen and block the mouse and keyboard of the remote computer.
Conclusion
What is RDP? This article introduces to you in detail the basic meaning, working principle, features, functions, usefulness, advantages and disadvantages, security issues, and safe use of RDP. It also introduces the operation steps of RDP so that you can better use it in daily life and work. In addition, you should use RDP safely, so that you can achieve remote control while further protecting your personal privacy and related data.
Besides, users also reflected that they often encounter problems like your credential did not work, user account did not work, and Windows 10 clipboard did not work when using RDP, making it more difficult to use it.