How to Reverse a Remote Desktop Connection [Simple Guide]
Delve into the world of secure remote access with a focus on remote desktop reverse connection. This article provides a detailed guide, compares AnyViewer as an alternative, and explores the advantages of mastering reverse connections for support, collaboration, and ethical use.
In the realm of remote access tools, security and versatility are paramount. Remote connections play a crucial role in support, collaborative work, and various other scenarios. This article explores the concept of reversing remote connections, providing a step-by-step guide. We'll also introduce an alternative tool as a reliable option and highlight the importance of secure remote access solutions.
How to Reverse a Remote Desktop Connection
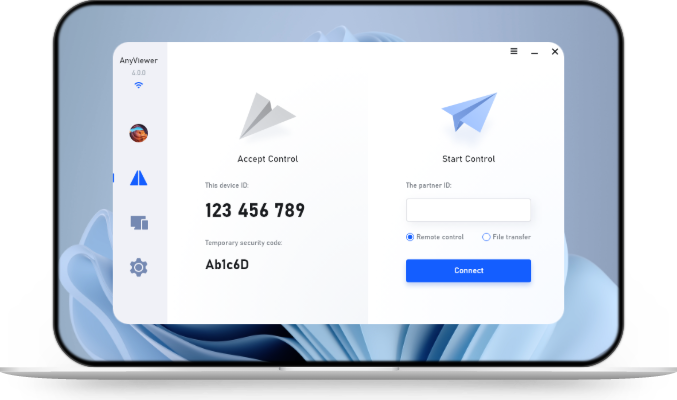
A reverse connection in remote access tools allows a user to access another computer without requiring the remote user to initiate the connection. This is particularly useful for support scenarios or collaborative work.
Step-by-Step Guide on Reversing a Remote Desktop Connection
Step 1. Tool Installation
Ensure that the remote access tool is installed on both the local and remote computers.
Step 2. Sharing Access Information
The remote user shares their access credentials or connection details with the local user.
Step 3. Initiating Connection
The local user initiates the connection process by inputting the provided access information.
Step 4. Accepting Connection
The remote user receives the connection request and grants permission, thereby enabling the local user to access their desktop remotely.
Bonus Tip: Ensuring Security and Ethical Considerations
While reversing remote connections can be a powerful tool, it's crucial to prioritize security and ethical use. Always ensure that you have explicit permission to access another computer and use encryption features provided by the remote access tool to secure the connection.
An Alternative for Remote Desktop Software: AnyViewer
AnyViewer is a robust remote access tool that competes with other remote access tools in the realm of secure connections. It offers a range of features for remote support, collaborative work, and presentations.
Comparison of Features with Other Remote Access Tools
AnyViewer shares similarities with a remote access tool, but also brings its unique features to the table:
- Cross-Platform Support: AnyViewer is compatible with various operating systems like Windows, macOS, iOS, and Android.
- Remote Support Capabilities: Both tools excel in providing support through remote connections.
- File Transfer: Seamlessly transfer files between devices using AnyViewer.
- Screen Wall: Real-time monitoring of multiple remote devices in a single window.
Highlighting AnyViewer as a Reliable Alternative
AnyViewer is a reliable alternative for users seeking secure and feature-rich remote access. It provides a user-friendly interface and a range of options for different use cases, making it a versatile choice.
Seamless Remote Access
You can operate a remote computer just like you would if you were physically there—moving the mouse, typing, and launching software without interruption. AnyViewer provides unattended access, allowing you to monitor and control multiple remote devices without requiring on-site approval. With built-in encryption and secure login features, it gives a trustworthy option for remote access, tech support, and IT administration.
Online File Transfer
During a remote session, you can easily and safely transfer files between your local and remote machines. AnyViewer makes this process simple by allowing you to either drag and drop items or choose specific files and folders to send, whether it’s documents, images, applications, or other data.
Live Chat in Text Box
The integrated chat feature allows both parties to communicate directly during a remote session, making it simple to give guidance, ask questions, or resolve problems without using an external messaging tool. This improves teamwork and boosts the effectiveness of remote support.
Screen Mirroring and Sharing
AnyViewer allows you to share your desktop or mobile screen live without giving full control to others. This feature is ideal for conducting presentations, training sessions, demos, or team discussions. Multiple participants can view the screen at the same time, which helps streamline communication, encourage collaboration, and simplify problem-solving. By providing a clear visual reference, screen sharing helps reduce confusion and boosts productivity during remote work and group activities.
Secure Role Permission Management
Team administrators can set customized access levels for each member, depending on their role. This ensures that only approved users can carry out certain tasks like managing devices, transferring files, or controlling remote systems. Assigning clear roles not only strengthens security and prevents unauthorized actions but also helps streamline operations and boost overall efficiency.
Exploring Secure Remote Access Solutions
Security is a top priority when dealing with a remote access tool. Look for features such as end-to-end encryption, multi-factor authentication, and secure connections to ensure the confidentiality of data during remote sessions.
Features to Look for in Secure Remote Access Solutions
- Encryption: Ensure that the remote access tool uses strong encryption methods to protect data transmission.
- Authentication Mechanisms: Implement multi-factor authentication for an additional layer of security.
- Logging and Monitoring: Choose tools that provide detailed logs and monitoring features for tracking remote sessions.
Balancing Convenience and Security in Remote Connections
While convenience is essential in remote access tools, finding the right balance with security features is crucial. Opt for tools that prioritize both aspects, ensuring a seamless yet secure remote access experience.
Advantages of Reversing Remote Connections
Facilitating Support and Troubleshooting
Reversing remote connections streamlines support procedures, enabling technicians to troubleshoot issues on remote devices without necessitating the remote user's initiation.
Collaborative Work Scenarios
In collaborative settings, reversing remote connections fosters seamless information sharing and collaborative problem-solving, thereby enhancing productivity and efficiency.
Ethical Considerations and Responsible Use
It's crucial to employ the capability of reversing remote connections ethically and responsibly. Always seek explicit consent before accessing another user's device, and prioritize data privacy and security at all times.
Conclusion
In conclusion, mastering secure remote access involves understanding and utilizing tools like remote access tool for reverse connections. This article provided a step-by-step guide on how to reverse remote access tool connection, introduced AnyViewer as a reliable alternative, and highlighted the importance of security in remote access tools. As users explore remote access solutions, it's essential to strike a balance between convenience and security for a seamless and protected experience.
FAQs
Can reversing remote access tool connection be done on different operating systems?
Yes, reversing remote access tool connection is supported across various operating systems, making it a versatile solution for users with different devices.
Does AnyViewer offer a free version with similar features to other remote access tools?
Yes, AnyViewer offers a free version with features comparable to other remote access tools, making it accessible for users with varying needs.
What security measures should I consider when using remote access tools for business purposes?
For business purposes, prioritize remote access tools with strong encryption, multi-factor authentication, and comprehensive logging and monitoring features to ensure data security and compliance.