Accessing Remote USB Ports Over Network: A Comprehensive Guide
Discover the seamless process of accessing remote USB ports over a network. Our guide covers step-by-step instructions, compatibility with Windows 10, and essential security measures. Unlock the potential of remote USB access with real-world case studies.
Introduction
In the digital age, the need for accessing USB ports remotely has become increasingly essential. Remote USB port access involves the ability to connect and utilize USB devices over a network. This can include printers, scanners, or external drives. The key features of this technology lie in its convenience and efficiency. Imagine seamlessly using a USB device plugged into a computer miles away – that's the power of remote USB port access.
Whether for flexibility in office setups or managing devices from a distance, understanding how to access remote USB ports over a network is a valuable skill. Let's delve into the intricacies of this process and explore the steps involved.
How to Access Remote USB Port Over Network
To embark on this journey, follow our step-by-step guide. The process involves simple steps, making it accessible even for those not well-versed in technical intricacies. After configuration, connecting to remote USB ports becomes a breeze.
Step 1. Software Installation
Start by installing specialized software designed for remote USB access. Look for reliable options that suit your specific needs and operating system. Once installed, the software will act as the bridge between the local and remote USB ports.
Here are some top remote USB access tools for your choice:
USB Network Gate (by Eltima Software)
- Supports Windows, macOS, Linux, and Android.
- Offers encryption, password protection, and advanced session control.
- Allows multiple users to connect to the same USB device (based on license).
FlexiHub
- Cloud-based USB over IP sharing solution.
- Secure and easy to set up, no need to configure IP addresses or port forwarding.
- Great for teams and enterprise use.
VirtualHere
- Lightweight and powerful.
- Ideal for Raspberry Pi and embedded systems.
- Offers both software and OEM integration.
Step 2. Configuration Settings
Configure the software settings to establish a secure connection. This may involve setting up user credentials, specifying the devices to be shared, and defining access permissions. Pay attention to security settings to ensure the protection of sensitive data during the remote access process.
Step 3. Connecting to Remote USB Ports
With the software installed and configured, connecting to remote USB ports becomes a straightforward process. Launch the software, identify the target device or USB port, and establish a connection. The remote USB device should now be accessible as if it were directly connected to your local machine.
Enhancing Security Measures
While the convenience of remote USB access is undeniable, security is paramount. Our guide offers best practices to secure the process, along with insights into potential risks and precautions. By implementing these measures, users can confidently access remote USB ports without compromising sensitive data.
Encryption Protocols
Implementing strong encryption protocols is a fundamental security measure. Utilize technologies such as SSL/TLS to encrypt the data transmitted between the local and remote devices during the USB access process. Encryption adds a crucial layer of confidentiality, making it significantly more challenging for unauthorized entities to intercept and access sensitive information.
Secure Authentication
Establishing secure authentication practices is essential for controlling access to remote USB ports. Enforce strong user authentication by requiring secure passwords or implementing multi-factor authentication (MFA). This ensures that only authorized users with verified identities can access and utilize remote USB devices. Robust authentication mechanisms significantly reduce the risk of unauthorized access.
Access Control
Implementing effective access control policies is crucial to limiting access to remote USB ports to only those who genuinely need it. Define and enforce access permissions, ensuring that users or devices without legitimate reasons are prevented from accessing USB devices remotely. Regularly review and update access control settings to adapt to changing security requirements and maintain a tight control over access points.
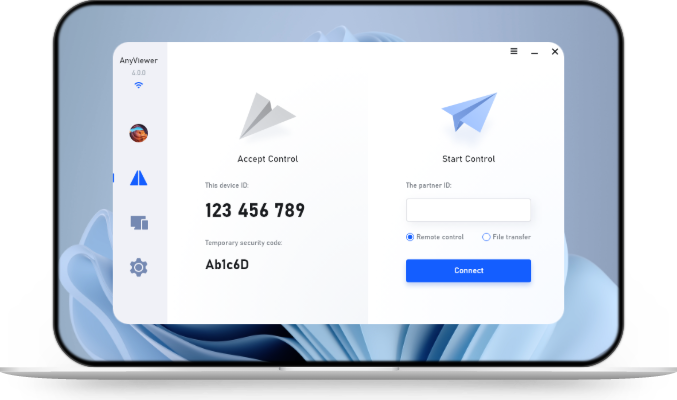
Bonus Tip: Access Remote USB Devices with Ease Using AnyViewer
While traditional methods to access a remote USB port over a network often involve complex configurations or third-party USB redirector tools, AnyViewer offers a much more user-friendly alternative for remote device access. Although it doesn’t provide direct USB redirection functionality like dedicated USB-over-IP software, AnyViewer allows you to remotely control a computer where the USB device is physically connected.
This means if you have a USB device (such as a flash drive, printer, or USB dongle) plugged into a remote Windows PC, you can use AnyViewer to take full control of that computer from another device—whether it’s a Windows PC, Mac, iOS, or Android device. Once connected, you can interact with the USB-connected software or files just as if you were sitting in front of the remote machine.
Why Choose AnyViewer?
- ✅ Cross-platform support – Control Windows/Mac from iOS, Android, or another Windows/Mac.
- ✅ Secure & fast connection – End-to-end encryption ensures safe data transmission.
- ✅ No complicated setup – Just log in, connect, and go—perfect for non-tech users.
If your goal is to access a USB device indirectly by operating the host PC remotely, AnyViewer is one of the simplest and most effective solutions available.
Conclusion
In conclusion, accessing remote USB ports over a network opens up new possibilities for device management and connectivity. Recap the key points from our guide and stay informed about future trends in this evolving field. With the right knowledge and tools, users can navigate the world of remote USB port access with confidence.
FAQs
- Is remote USB access secure?
Remote USB access can be secure if proper measures are taken, such as using encrypted connections and following the best practices outlined in our guide.
- Can I access remote USB ports on older Windows versions?
While our guide focuses on Windows 10, the principles can be applied to older versions with some adjustments. Consult the software documentation for compatibility details.
- Are there limitations to remote USB access over a network?
Like any technology, remote USB access has limitations, such as potential latency issues. Understanding these limitations helps users make informed decisions.