What Is RDP Security Layer?
This post mainly introduces three different types of RDP security layers, the way to configure a specific security layer for RDP connections, and the tips for securer RDP connections.
Security concern of RDP
With the popularity of RDP, more and more of its vulnerabilities were revealed. One of the most famous vulnerabilities may be the man-in-the-middle attacks, which may intercept the connection between the client and the server, compromising the communication in the process. Other vulnerabilities include Key-logging attacks (hackers create sophisticated malware that tracks all the keys users press on their keyboards while accessing RDS) and EternalBlue attacks (hackers execute arbitrary codes remotely, giving them access to the network) also bring great threat to the safety of RDP connection.
Three different types of RDP security layers
To secure RDP connections, there are three types of security layers for RDP communications: Negotiate, RDP, and SSL. Next, we’ll introduce them one by one.
Negotiate
The Negotiate method enforces the most secure approach that the client supports. RDS sessions use the Negotiate technique by default. The usage of the Negotiate method requires Transport Layer Security (TLS) version 1.0. The Negotiate technique is used to authenticate the RD Session Host server if TLS is provided. If TLS is not available, RDP (discussed further below) will be utilized to secure communications, but the RD Session Host server will not be authenticated.
RDP
The RDP method encrypts communications between the client and the RD Session Host server using native RDP encryption. As previously stated, if this method is selected, the RD Session Host server will not be authenticated. It is not recommended to use native RDP encryption.
SSL (Secure Sockets Layer)
The SSL method verifies the identity of the RDSH server and encrypts all connections between the client and the server using the TLS 1.0 protocol. The connection will fail if TLS is not supported. This security layer is recommended for RDP connections.
How to configure a specific security layer for RDP connections
In this section, we’ll introduce how to configure a specific security layer for RDP connections. Follow the steps below.
Step 1. Press Win + R, then type in “gpedit.msc” and press OK to open the Local Group Policy Editor window.
Step 2. Navigate here: Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security.
Step 3. Find and click Require use of specific security layer for remote connections, then change its status to Enabled. Choose the security layer (Negotiate, RDP, SSL) from the drop-down list.
Ways to secure RDP connections
To reduce RDP risk, there are some tips to help users secure their RDP connections.
- Use complex passwords. Using strong and complicated passwords makes brute-force RDP attacks more difficult to execute.
- Use a Firewall to restrict access. Firewall rules can be written to restrict Remote Desktop access so that only a certain IP address or range of IP addresses can connect to a given device.
- Require multi-factor authentication (MFA). MFA is a strong method of preventing brute-force and key-logging attacks. When MFA is utilized, it establishes layered security, making it more difficult for hackers to get access to the RDS infrastructure.
- Enable automatic updates on the operating systems. Updating the operating systems for both the client and the RDSH server to the most recent versions eliminates known RDP vulnerabilities.
Safe & secure remote desktop software: AnyViewer
Another way to achieve secure remote connections is to use the safe third-party remote desktop software AnyViewer. Developed by a strong technical team and secured by Elliptic Curve Cryptography (ECC) encryption, it provides you with a fast and stable remote access connection, and at the same time, protects your data from leakage.
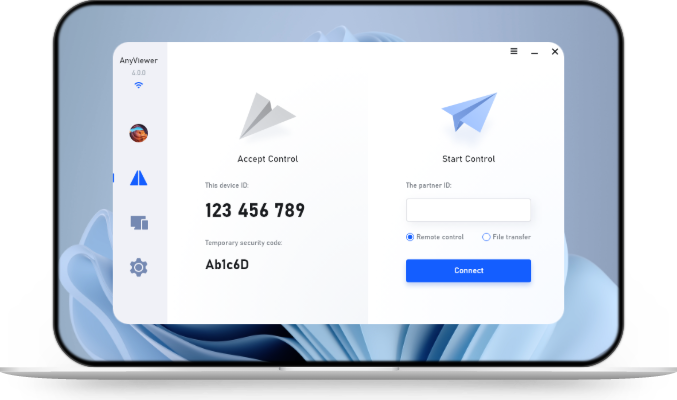
AnyViewer provides you with two methods to achieve secure remote connections. One is to send a control request and another is to input a security code to achieve unattended remote access.
Part 1. For unattended remote access with one-click
Step 1. Install and launch AnyViewer on both computers. Go to Log in, and then click Sign up. (If you already have signed up on its official website, you can log in directly.)
Step 2. Fill in the signup information.
Step 3. Then you can see you successfully logged in to AnyViewer. Your device will automatically be assigned to the account you've logged in to.
Step 4. Log in to the same AnyViewer account on the two devices, then click One-click control to achieve unattended remote access. You can also transfer files between computers.
Part 2. Two connection methods of AnyViewer
To better protect your privacy, you can also achieve remote control via AnyViewer without logging in to it. But we should note you that some features like file transfer and screen share can't be used if you are not logged in to AnyViewer.
Connection method 1. Send a control request
Step 1. On the client computer, input the device ID of the host computer and then click Connect.
Step 2. Click Send a control request to your partner.
Step 3. On the host computer, click Allow to make the connection successful.
Connection method 2. Input security code
Step 1. On the host computer, go to Settings > Recipient. Tick the third option and then set the permanent security code.
Step 2. On the client computer, input the device ID of the host computer and then click Connect. Choose Input security code and enter the code. Click OK to achieve remote access.
Conclusion
What is the RDP security layer? There are three different types of RDP security layers: Negotiate, RDP, and SSL. Among these, Negotiate is the most secure approach which is used by RDS sessions by default. Besides, you can use the secure third-party remote desktop software AnyViewer as well. The ECC encryption algorithm it uses will secure your whole remote session.